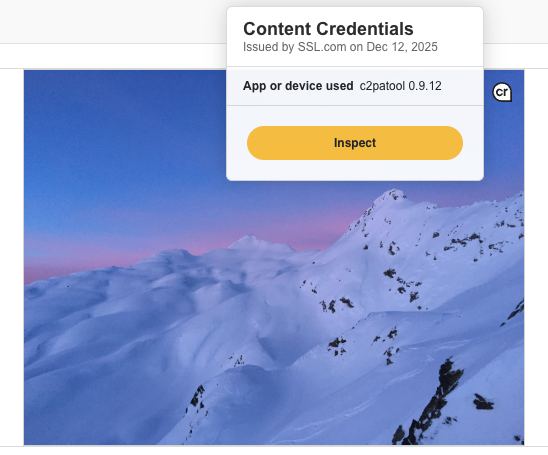
Content Credentials, sometimes referred to as the nutritional facts of online assets, is an open technology to help fact-check what we see online. Content Credentials are implemented via the C2PA (Coalition for Content Provenance and Authenticity) standard and adoption is accelerating across numerous major platforms, as enterprises recognize the critical need for Content Credentials, the digital “ledger” that provides tamper-evident information about provenance data. Content Credentials specifies exactly when and how the content was created, and further actions taken by products to alter it, thereby providing a verifiable record of the content’s origin and modifications.
To be validated, Content Credentials must be signed by a C2PA-conformant certification authority. Choosing the right certificate authority becomes a strategic decision that impacts your entire content authenticity infrastructure.
SSL.com, a globally trusted certificate authority, is one of the first certificate authorities that can deliver C2PA-conformant certificates, signing services (through our eSigner service), and custom integrations you need to protect online content , your brand, and your customers from altered media.
Contact Us Now for C2PA Solutions
You can currently access our C2PA Developer Tool to test SSL.com C2PA API endpoints.
C2PA: An Overview
The foundational value propositions of C2PA are comprised of:- Authentication – Cryptographically signs the content to prove its origin and verify that it hasn’t been tampered with since creation.
- Transparency – Creates an auditable trail showing every modification, edit, and transformation applied to the content throughout its lifecycle.
- AI Disclosure – Alerts whether the content was generated or modified using artificial intelligence tools, addressing concerns about deepfakes, altered, and synthetic media.
- Manifest – Embedded container holding the content’s full provenance history, that gets attached to the digital media (e.g., video, images, audio, documents, etc.)
- Assertions – Individual facts (i.e., camera types, edits, AI involvement) about the content’s state.
- Claims – A signed package bundling assertions, identifying the generator, and linking to parent content.
- Signature – Public key infrastructure (PKI)-based, cryptographic seal to prove identity and ensure the claim is unaltered.
The Difference Between CAWG and C2PA Signatures
A CAWG identity signature authenticates who created it, while a C2PA manifest signature authenticates the provenance information, ensuring an unbroken chain of trust from creation to publication.
The CAWG (Creator Assertions Working Group) is building on C2PA to define technical standards that empower individuals and organizations to assert attribution of digital content while supporting privacy and transparency. Understanding the difference between a CAWG signature and a C2PA signature in an identity assertion is crucial for proper content provenance. Both are cryptographic seals, but they serve different, complementary purposes in establishing digital trust. CAWG signatures are tied to the content creators. These can be individuals, organizations, or both. S/MIME or Document Signing Certificates can be used to link the artifact to a specific person or organization, enhancing personal accountability and preventing others from claiming the creator’s work as their own.
In contrast, C2PA signatures authenticate a generator of claims: that is, a tool that generates provenance information. This could, for instance, be a cam recorder, a mobile phone, or an audio editing tool. This confirms that the published file and its attribution are authentic and have not been tampered with since publication.
| C2PA Manifest Signature | CAWG Identity Signature | |
| Purpose | Identifies provenance (tools), proves the integrity of the manifest | Asserts which individual(s) or organizations created or contributed to the content |
| What is signed | The C2PA manifest (set of claims) | An identity assertion |
| Required? | Yes | Optional |
| Trust Model | C2PA Trust List | Domain-specific trust lists, e.g., IPTC Verified News Publishers List |
| Certificate type | X.509 from a C2PA Trusted CA (e.g., SSL.com) | S/MIME or Document Signing certificate linked to the IPTC Origin Verified News Publishers List or the to the Mozilla Root store (e.g., SSL.com) |
| Represents | A generator (a tool, a device, etc.) | A human or organization (an identity) |
| What does it help to conclude? | “This is an authentic provenance manifest.” | “This is who claims to have contributed to the content.” |
Why SSL.com Is the Clear Choice for Enterprise C2PA Implementation
Complete End-to-End C2PA Infrastructure
As a publicly trusted certificate authority (CA), SSL.com helps your business deploy C2PA solutions at scale. SSL.com offers our customers:- C2PA Certificate Issuance – Enterprise-grade certificates that sign content authenticity information directly into your digital assets are intended to work with all C2PA-conformant validation processes designed for high-volume content creation environments.
- Global Trust Infrastructure: Our C2PA root certificates are publicly listed in the C2PA Trust Lists, ensuring immediate validation of your Content Credentials by all compliant verifiers.
- Custom PKI Integration – Tailored solutions that integrate seamlessly with your existing content management systems, creative workflows, and publishing pipelines without disruption to current operations.
- Trusted Timestamp Authority Services: To provide independent proof that signing was performed at a stated point in time, SSL.com is a C2PA-conformant Time Stamp Authority, as indicated by our Root certificate, publicly recorded in the C2PA TSA Trust List.
Proven Enterprise PKI Expertise Since 2002
With over two decades of experience as a globally-trusted certificate authority, SSL.com brings unmatched expertise to C2PA implementations. Our vast understanding of enterprise certificate lifecycle management, tailoring PKI solutions, and meeting compliance requirements ensures your content authenticity program launches successfully and operates reliably at scale.Scalable Certificate Management: Automated provisioning, renewal, and revocation processes designed for enterprise content volumes.
Enterprise Support: Dedicated C2PA-knowledgeable consultants provide hands-on guidance from initial planning through full deployment and ongoing optimization.
Compliance-Ready Architecture: As content authenticity regulations emerge globally, SSL.com’s C2PA implementation provides the documentation, audit trails, and security controls needed to demonstrate compliance with evolving legal requirements.
Advanced Media File Protection Capabilities
Our C2PA solutions support a comprehensive range of digital assets, including images, video, audio, text, and digital documents, with cryptographic binding that remains in place even during format conversions and platform transfers. This ensures your Content Credentials remain intact as your digital media files move through complex distribution chains.As an active C2PA member, SSL.com stays ahead of specification updates and emerging requirements. We ensure that your implementation remains current with the latest standards and security enhancements, meeting both your immediate business needs and long-term content authenticity strategies.
Start Now: Secure Your Content Using C2PA Certificates
SSL.com’s proven certificate authority expertise, comprehensive C2PA certificate support, and enterprise-grade solutions provide the foundation your organization needs to be a leader in the era of content authenticity, including integration with emerging AI detection tools and evolving platform requirements. Using C2PA certificates can help authenticate and prove the provenance of your video and audio files, and a range of other digital content assets, from claims made by malicious actors and deepfakes.Contact our C2PA consultants today to design a customized implementation that protects the integrity of digital assets, enhances customer trust, and positions your organization as a leader in content authenticity.
Additionally, you can access our C2PA Developer Tool to test SSL.com C2PA API endpoints.
Contact Us Now for C2PA Solutions
Was this article helpful?
Thanks for your feedback!