This is a guide on how Azure DevOps can be integrated with eSigner CodeSignTool to perform automated code signing.
CodeSignTool is a command line utility that is suitable for cloud code signing processes and seamlessly integrates with various CI/CD platforms. It forms part of eSigner: our remote signing service that offers an efficient, secure, and user-friendly approach to code signing.
Environment Variables
- USERNAME: SSL.com account username. (Required)
- PASSWORD: SSL.com account password (Required)
- CREDENTIAL_ID: Credential ID for signing certificate. If credential_id is omitted and the user has only one eSigner code signing certificate, CodeSignTool will default to that. If the user has more than one code signing certificate, this parameter is mandatory. (Required)
- TOTP_SECRET: OAuth TOTP Secret. You can access detailed information on https://www.ssl.com/how-to/automate-esigner-ev-code-signing (Required)
- ENVIRONMENT_NAME : ‘TEST’ or ‘PROD’ Environment. (Required)
Inputs
- input_file_path: Path of code object to be signed. (Required)
- output_dir_path: Directory where signed code object(s) will be written. If output_path is omitted, the file specified in -file_path will be overwritten with the signed file.
Create a project on visualstudio.com
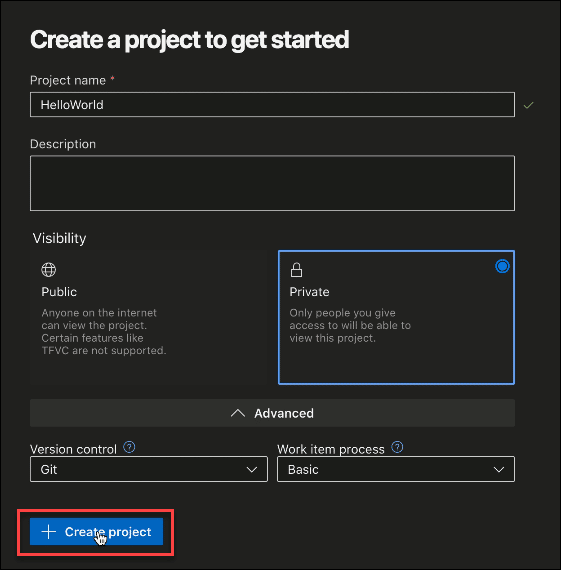
Create a new .yml file on your code editor
Set integration triggers and environment variables
Continuous integration triggers
trigger:
– none
Defines environment variables globally. Job level property overrides global variables
variables:
buildConfiguration: ‘Release’
Group jobs into stages
Write the steps for the build stage. All jobs in one stage must be completed before the next stage is executed.
stages:
– stage: build
# When the workflow runs, this is the name that is logged
displayName: Build
jobs:
– job:
pool:
Run job on Windows VMs
vmImage: ‘windows-latest’
steps:
Install Dotnet 6.0.x
– task: UseDotNet@2
displayName: ‘Install .NET Core SDK’
inputs:
version: ‘6.0.x’
performMultiLevelLookup: true
includePreviewVersions: true
Restore Dotnet project
– task: DotNetCoreCLI@2
displayName: Restore
inputs:
commmand: ‘restore’
Build dotnet project with Release configuration
– task: DotNetCoreCLI@2
displayName: Build
inputs:
commmand: build
projects: HelloWorld.csproj
arguments: ‘–configuration $(buildConfiguration)’
Create directories for signed artifacts
– powershell: New-Item -ItemType Directory -Path ./artifacts
displayName: ‘Created directories for artifacts’
Create directories for signed packages
– powershell: New-Item -ItemType Directory -Path ./packages
displayName: ‘Created directories for packages’
Copy artifact to be signing path
– powershell: Copy-Item ./bin/Release/netcoreapp3.1/HelloWorld-0.0.1.dll -Destination ./packages/HelloWorld.dll
displayName: “Copy built artifacts to packages directory”
Save artifact in order to use signing job
– task: PublishBuildArtifacts@1
displayName: ‘Save to be signed artifact for downloading’
inputs:
pathtoPublish: ./packages/HelloWorld.dll
artifactName: HelloWorld.dll
Write the steps for the Sign stage
– stage: Sign
# When the workflow runs, this is the name that is logged
displayName: Sign
jobs:
– job:
pool:
Run job on Ubuntu VMs
vmImage: “Ubuntu-latest”
steps:
Create directories for signed artifacts
– script: mkdir -p ./artifacts && mkdir -p ./packages
displayName: “Created directories for artifacts and packages”
Download the artifact to be signed
– task: DownloadPipelineArtifact@2
inputs:
artifact: HelloWorld.dll
downloadPath: ./packages
Install Docker 17.09.0-ce
– task: DockerInstaller@0
displayName: Docker Installer
inputs:
dockerVersion: 17.09.0-ce
releaseType: stable
Docker Pull CodeSigner Docker Image
– script: docker pull ghcr.io/sslcom/codesigner:latest
displayName: ‘Docker Pull CodeSigner Docker Image’
Sign artifact with CodeSigner docker image
– script: docker run -i –rm –dns 8.8.8.8 –network host –volume $PWD/packages:/codesign/examples –volume $PWD/artifacts:/codesign/output
-e USERNAME=$(USERNAME) -e PASSWORD=$(PASSWORD) -e CREDENTIAL_ID=$(CREDENTIAL_ID) -e TOTP_SECRET=$(TOTP_SECRET)
-e ENVIRONMENT_NAME=$(ENVIRONMENT_NAME) ghcr.io/sslcom/codesigner:latest sign -input_file_path=/codesign/examples/HelloWorld.dll
-output_dir_path=/codesign/output
displayName: ‘Sign artifact with CodeSigner docker image’
Save signed artifact for downloading
– task: PublishBuildArtifacts@1
displayName: ‘Save signed artifact for downloading’
inputs:
pathtoPublish: ./artifacts/HelloWorld.dll
artifactName: HelloWorld.dll
Create a new .gitignore file
Type in:
bin
obj
.vscode
On the message bar, type in Created pipeline.yml and click the Commit button
Proceed to click the Sync Changes button
Proceed to visualstudio.com and click Repos on the dashboard
Refresh the page to see the yml file
Click Pipelines on the dashboard
Next, click Create Pipeline
Click Azure Repos Git
Select your YAML file
Click Variables button followed by New variable
Place the value for each environment variable and click the OK button
Click the + sign to keep on adding each variable
After placing in all variables, proceed to create your pipeline
Run your pipeline
Click Pipelines on the dashboard. Click the three-dots (more options) on your pipeline. Click Run pipeline. Finally, click the Run button.
Click Build to start the build stage
Check if each job in the build stage is successful
Click the drop-down arrow beside Job to see the status of each build job
Initiate the Sign stage by clicking Job
Check if each step in the signing process is successful
Double check if both build and sign stages are successful
Sample Azure DevOps Pipeline
Check out the sample Azure DevOps pipeline we have created on github.com/SSLcom/codesigner-azuredevops-sampleOther Remote Signing Integration Guides
- Cloud Code Signing Integration with CircleCI
- Cloud Code Signing Integration with GitHub Actions
- Cloud Code Signing Integration with GitLab CI
- Cloud Code Signing Integration with Travis CI
- Cloud Code Signing Integration with Jenkins CI
- Cloud Code Signing Integration with BitBucket
- Cloud Code Signing Automation with CI/CD Services
Need Custom Solutions?
With our expert knowledge and five-star support staff, we’re ready and willing to work with you on custom solutions or enterprise-level high-volume signing discounts. Fill out the form below and we’ll be in touch.