All versions of the SSL/TLS protocol prior to TLS 1.2 are now deprecated and considered insecure. Many web server platforms still have TLS 1.0 and TLS 1.1 enabled by default. However, all modern web browsers are compatible with TLS 1.2. For this reason, it’s a good idea for website owners to check their server configuration to make sure that only current, secure versions of SSL/TLS are enabled and all others (including TLS 1.0, TLS 1.1, and SSL 3.0) are disabled.
This guide includes instructions for checking which versions of SSL/TLS are enabled on a website, disabling obsolete versions of SSL/TLS in Apache and Nginx, and shows examples of browser errors resulting from servers running only deprecated, insecure versions of SSL/TLS.
Check Enabled SSL/TLS Versions
Online Tools
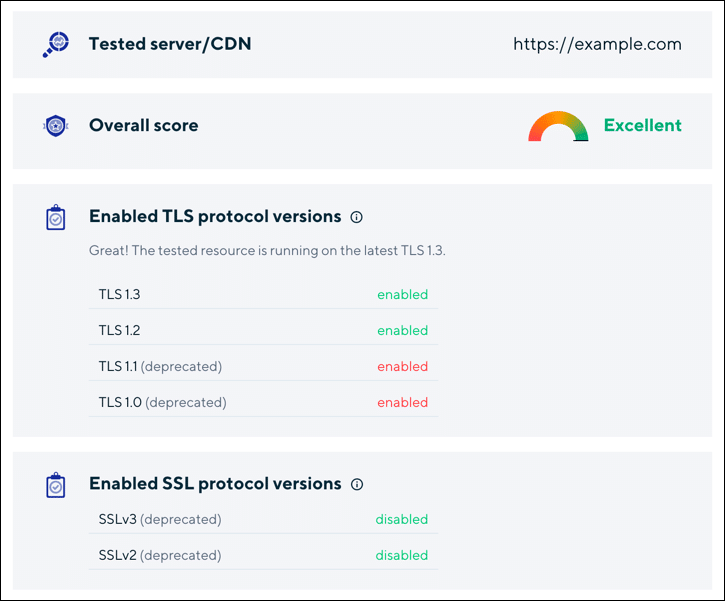
You can quickly check the versions of SSL/TLS your website supports by visiting CDN77’s TLS Checker and entering the domain name you’d like to check. As can be seen below, https://example.com currently disables SSL versions 2 and 3, but enables all versions of TLS (including the deprecated TLS 1.1 and 1.0):
Nmap
You can also check for the SSL/TLS versions and ciphers supported by a website with the open-source nmap command-line tool:
nmap --script ssl-enum-ciphers -p <PORT> <DOMAIN NAME>
The default port for SSL/TLS is 443. The command below will generate a report for example.com:
$ nmap --script ssl-enum-ciphers -p 443 example.com Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-25 13:10 EDT Nmap scan report for example.com (93.184.216.34) Host is up (0.031s latency). Other addresses for example.com (not scanned): 2606:2800:220:1:248:1893:25c8:1946 PORT STATE SERVICE 443/tcp open https | ssl-enum-ciphers: | TLSv1.0: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A | TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 2048) - A | TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 2048) - A | TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 2048) - A | TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 2048) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 2048) - A | TLS_DHE_RSA_WITH_SEED_CBC_SHA (dh 2048) - A | TLS_RSA_WITH_SEED_CBC_SHA (rsa 2048) - A | compressors: | NULL | cipher preference: server | TLSv1.1: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A | TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 2048) - A | TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 2048) - A | TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 2048) - A | TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 2048) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 2048) - A | TLS_DHE_RSA_WITH_SEED_CBC_SHA (dh 2048) - A | TLS_RSA_WITH_SEED_CBC_SHA (rsa 2048) - A | compressors: | NULL | cipher preference: server | TLSv1.2: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A | TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (dh 2048) - A | TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (dh 2048) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A | TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 (dh 2048) - A | TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 2048) - A | TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 (dh 2048) - A | TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 2048) - A | TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A | TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 2048) - A | TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 2048) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 2048) - A | TLS_DHE_RSA_WITH_SEED_CBC_SHA (dh 2048) - A | TLS_RSA_WITH_SEED_CBC_SHA (rsa 2048) - A | compressors: | NULL | cipher preference: server |_ least strength: A Nmap done: 1 IP address (1 host up) scanned in 3.88 seconds
Server Configuration
Apache
To disable TLS 1.0 and 1.1 in Apache, you will need to edit the configuration file containing the SSLProtocol directive for your website. This file may be located in different places depending on your platform, version, or other installation details. Some possible locations are:
/usr/local/apache2/conf/extra/httpd-ssl.conf(default Apache installation)/etc/apache2/mods-enabled/ssl.conf(Ubuntu/Debian)/private/etc/apache2/extra/httpd-ssl.conf(macOS)
When you have located the correct configuration file, look for a line beginning with SSLProtocol. This example, from a default macOS Apache installation, disables SSLv3 with the - operator but enables TLS 1.0 and 1.1:
SSLProtocol all -SSLv3
You can disable all obsolete versions of SSL/TLS supported by Apache by specifying them as follows:
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1
The configuration above enables TLS 1.2, as well as TLS 1.3 if it is available in your environment.
Apache and Virtual Hosts
Apache can run more than one web site on a single server. These virtual hosts may be based on IP number, port, or domain name, and may include settings that override the base configuraton for Apache. For this reason, you should check the settings for each virtual host in your configuration files, especially if your changes to the base SSL/TLS configuration do not seem to be working.
For versions of Apache prior to 2.4.42 (built/linked against OpenSSL before 1.1.1), it was not possible to specify different SSL/TLS protocols for name-based virtual hosts sharing the same base IP number and port – the SSLProtocol of the first virtual host was applied to all others. Beginning with Apache 2.4.42/OpenSSL 1.1.1, the SSLProtocol of each name-based virtual host is honored when the Server Name Indication (SNI) is provided by the client during the SSL/TLS handshake.
Once you have made your configuration changes, reload Apache to put them into effect. For more information on the SSLProtocol directive, please refer to Apache’s documentation.
Nginx
SSL/TLS protocol settings may be specified in the primary Nginx configuration file (usually located at /etc/nginx/nginx.conf), or in your site configuration files. Look for a line beginning with ssl_protocols. For example, the following is from the default nginx.conf file from a fresh Nginx install on Ubuntu:
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3; # Dropping SSLv3, ref: POODLE
You can edit this line so that only current, secure versions of SSL/TLS are included:
ssl_protocols TLSv1.2 TLSv1.3;
Note that any settings in your default SSL configuration may be overridden by server blocks configuring individual domain names, so be sure to check for those if changes to your protocol settings are not reflected in your website.
Once you have made your configuration changes, reload Nginx to put them into effect. For more information, please refer to Nginx’s documentation on configuring HTTPS servers.
TLS 1.0 and 1.1 Browser Errors
Because TLS versions 1.0 and 1.1 are currently regarded as insecure, most modern browsers will produce an error message if they encounter a website where these obsolete TLS versions are enabled but TLS 1.2 or 1.3 is not. Examples of these errors are shown below:
Google Chrome
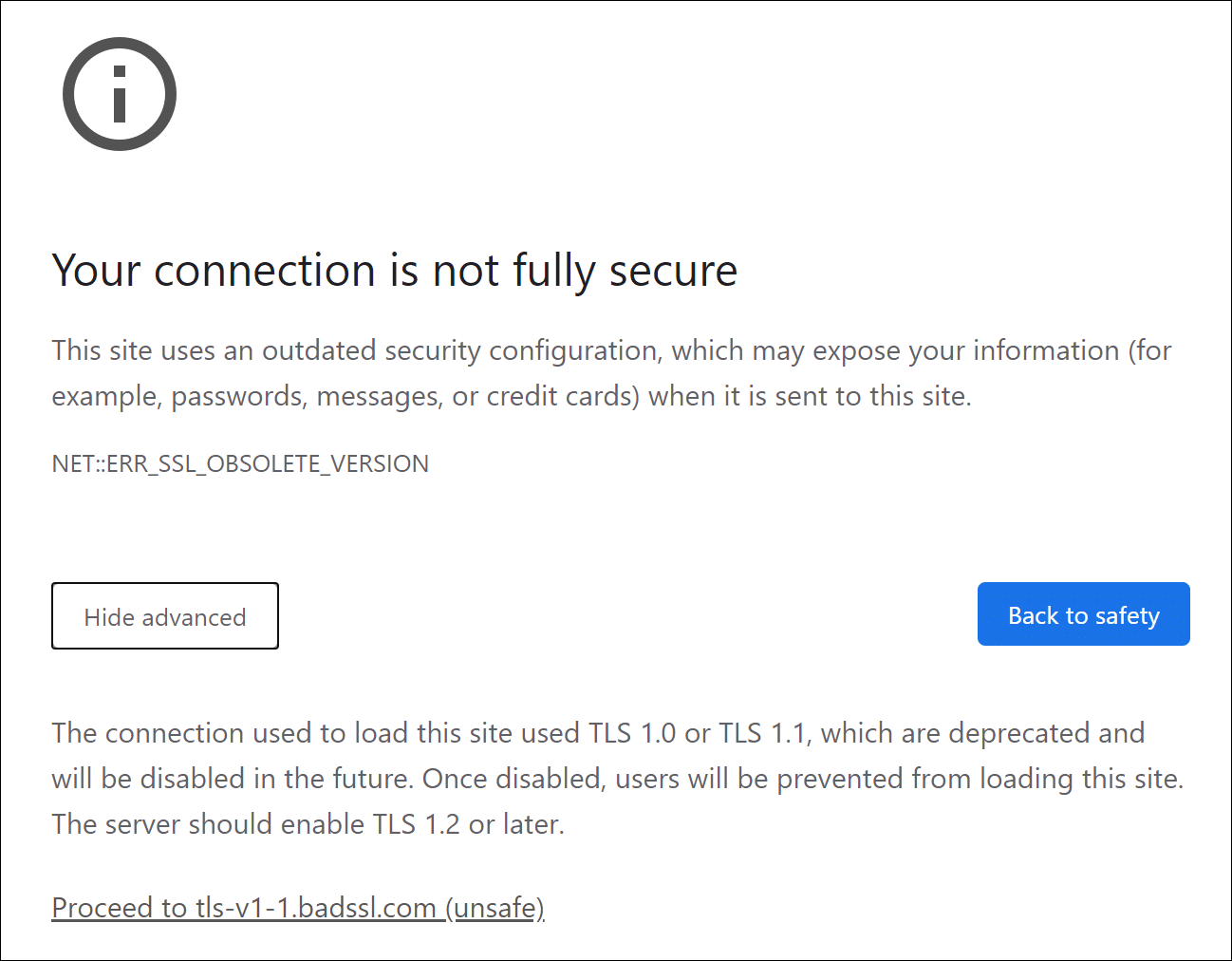
Google Chrome displays the following error message when it connects to a website running TLS 1.0 or 1.1:
Your connection is not fully secure
This site uses an outdated security configuration, which may expose your information (for example, passwords, messages, or credit cards) when it is sent to this site.NET::ERR_SSL_OBSOLETE_VERSION
The connection used to load this site used TLS 1.0 or TLS 1.1, which are deprecated and will be disabled in the future. Once disabled, users will be prevented from loading this site. The server should enable TLS 1.2 or later.
Mozilla Firefox
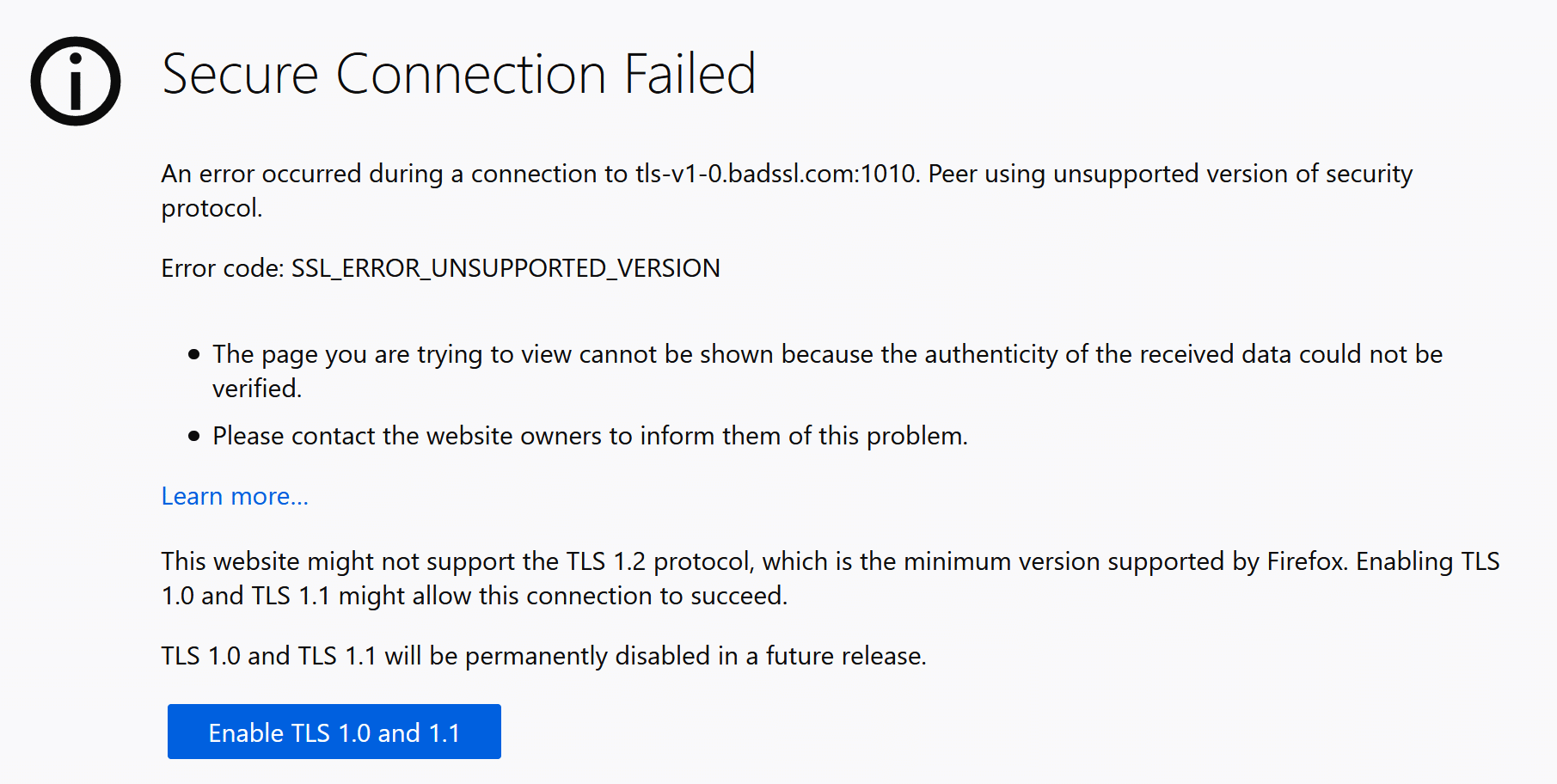
Mozilla Firefox produces the following error message when it connects to a website running TLS 1.0 or 1.1:
Secure Connection Failed
An error occurred during a connection to [URL]. Peer using unsupported version of security protocol.
Error code:SSL_ERROR_UNSUPPORTED_VERSION…
This website might not support the TLS 1.2 protocol, which is the minimum version supported by Firefox. Enabling TLS 1.0 and 1.1 might allow this connection to succeed.
TLS 1.0 and TLS 1.1 will be permanently disabled in a future release.
Apple Safari
Apple’s Safari browser will load HTTPS websites using TLS 1.0 and 1.1, but will display a “Not Secure” message in the browser’s address bar.
For More Information
To read about the security issues associated with earlier versions of TLS, please read our article, Deprecating early TLS for a safer Internet. For more information about the important differences between TLS 1.2 and TLS 1.3, check out TLS 1.3 is here to stay.
And, as always, if you have any questions, please contact us by email at Support@SSL.com, call 1-877-SSL-SECURE, or just click the chat link at the bottom right of this page. You can also find answers to many common support questions in our knowledgebase. Thank you for visiting SSL.com!
SSL.com provides a wide variety of SSL/TLS server certificates for HTTPS websites, including: