PKI (Public Key Infrastructure) relies on public and private keys to encrypt data. Hardware Security Modules (HSMs) safeguard these keys in tamper-proof boxes. HSMs store and manage the keys, preventing theft or misuse. They’re vital for PKI security, enabling trusted online transactions and communications. This article explains why HSMs are so critical for PKI and online safety.
The Role of Public Key Infrastructure in Encryption, Certificate Management, and Secure Communication
PKI fulfills various important functions. It provides a strong foundation for building trust, maintaining confidentiality, and facilitating secure transactions. The following are the expanding uses of PKI in digital communication:
-
Encryption: PKI facilitates encryption and decryption, allowing for safe communication. When Alice wants to send an encrypted message to Bob, she encrypts the message with Bob’s public key. Only Bob, who has the corresponding private key, can decrypt and read the message. This ensures that the news is kept private even if enemies intercept it.
-
Certificate Management: PKI entails digital certificate production, administration, distribution, usage, storage, and revocation. After authenticating an entity’s identity, Certificate Authorities issue certificates. These certificates establish trusted identities, validate digital content’s integrity, and enable secure communication.
-
Digital Signatures: PKI allows for creating and validating digital signatures, which offer non-repudiation and integrity for digital content. When Alice digitally signs a document using her private key, anyone with her public key may confirm that she signed the document and has not been tampered with since the signature was applied. For more detailed information on record signing certificates and digital signatures, you can visit our comprehensive guide at Document Signing Certificates – SSL.com.
-
Secure Internet Browsing: PKI is the foundation for safe web browsing through technologies such as Transport Layer Security (TLS) and its precursor, Secure Sockets Layer (SSL). These protocols provide secure connections between web browsers and servers, ensuring that sensitive data sent over the internet is encrypted and secure.
-
Secure Email: Using digital certificates, PKI provides secure email transmission. PKI maintains the authenticity and secrecy of email content by digitally signing and encrypting it, preventing unauthorized access or tampering. For more detailed information on sending a secure email using S/MIME (Secure/Multipurpose Internet Mail Extensions), you can visit our comprehensive guide at Secure Email Guide with S/MIME.
-
IoT (Internet of Things) Security: With the development of IoT devices, PKI plays an important role in securing device connections and maintaining the integrity of sent data. Using digital certificates, PKI allows device authentication, secure firmware updates, and data encryption in IoT ecosystems. For more detailed information on securing the Internet of Things (IoT) with SSL/TLS (Secure Sockets Layer/Transport Layer Security), you can visit our comprehensive guide at Securing the Internet of Things (IoT) with SSL/TLS.
Understanding PKI’s extensive uses and integration into numerous facets of digital communication and cybersecurity is critical for understanding the importance of HSMs in enhancing PKI security.
The Role of Hardware Security Modules in Public Key Infrastructure
Hardware Security Modules (HSMs) play an important role in increasing the security of Public Key Infrastructure (PKI) by providing a secure environment for maintaining and safeguarding cryptographic keys. HSMs are specialized hardware devices that use strong physical and logical security techniques to keep important keys safe from illegal access and alteration.
Improving Key Security
HSMs’ principal function is to protect cryptographic keys used in PKI. Key management systems (HSMs) provide a secure environment for key production, storage, and access control. HSMs improve key security in the following ways:
Generation of Secure Keys: HSMs create cryptographic keys within their safe hardware and provide a reliable source of random numbers. This protects the keys’ integrity and strength by shielding the generation process from external manipulation or compromise.
Tamper-Proof and Tamper-Evident Design: Physical security methods are built into HSMs, making them tamper-evident and tamper-proof. They have reinforced casings, tamper detection sensors, and self-destruct mechanisms that activate in the event of unwanted access or modification of the device. These safeguards guard against physical attacks, such as tampering or extracting important keys.
Key Storage Security: HSMs securely store cryptographic keys within their hardware, preventing illegal access. The keys are encrypted and kept in a secure memory that cannot be tampered with or extracted. The keys remain safe even if an attacker physically gains access to the HSM.
Resource-Intensive Operations Offloading
HSMs improve efficiency by outsourcing computationally intensive cryptographic processes from the software layer to dedicated hardware. This offloading is beneficial in several ways:
Improved Cryptographic Operations: HSMs are purpose-built devices that excel in efficiently executing cryptographic operations. Organizations may dramatically increase the speed and performance of cryptographic activities such as key creation, signing, and decryption by exploiting the specialized hardware within the HSM.
Lower Processing Load: Offloading cryptographic activities to HSMs frees up processing power on servers or other devices, allowing them to concentrate on more important duties. This enhancement enhances overall system performance and scalability, particularly in contexts with a high volume of cryptographic operations.
Defense Against Side-Channel Attacks: Side-channel attacks, which exploit information spilled during cryptographic operations, are designed into HSMs. HSMs’ dedicated hardware aids in mitigating these attacks by safeguarding the confidentiality of important keys.
Authorization and Access Control
HSMs include strong access control features to ensure that only authorized individuals or processes can access and use cryptographic keys. Among the access control measures are:
Authentication: To access the stored keys, HSMs require authentication techniques such as passwords, cryptographic keys, or biometric elements. This prohibits unauthorized users from accessing or extracting the keys.
Policies for Authorization: Organizations can use HSMs to set granular authorization policies describing which entities or processes can access specific keys and perform cryptographic actions. This helps to implement the concept of least privilege by preventing key misuse or unauthorized use.
Auditing and Documentation: HSMs keep detailed audit logs of key management activities such as key usage, access attempts, and configuration modifications. Organizations can use these logs to monitor and review key operations, spot abnormalities, and guarantee compliance with security regulations.
The role of HSMs in PKI is crucial for cryptographic key protection, offloading resource-intensive processes, and implementing strict access control mechanisms. Organizations may improve their PKI installations’ security, scalability, and performance by employing HSMs.
Cloud HSMs for Document and Code Signing
As more businesses adopt cloud computing, there is a greater need for secure key management solutions in the cloud. Hardware Security Modules (HSMs) are now available as a service (HSMaaS) from cloud providers and HSM vendors, enabling safe settings for key creation and storage. This section will look at the cloud HSMs supported for document signing. EV and OV code signing certificates, their capabilities, and the important procedures associated with their use.
Overview of Cloud HSMs Supported
SSL.com currently supports several cloud HSM services for issuing Adobe-trusted document signing certificates and code signing certificates. Let’s look at three popular cloud HSM offerings in more detail:

AWS CloudHSM: Amazon Web Services (AWS) is a cloud computing platform. CloudHSM is a service that provides FIPS 140-2 Level 3 approved HSMs in the cloud. AWS CloudHSM offers dedicated HSM instances physically situated within AWS data centers. It supports safe key storage and cryptographic operations and includes key backup and high availability.
Azure Dedicated HSM: Azure Dedicated HSM is the product of Microsoft Azure’s hardware security module. It validates HSMs to FIPS 140-2 Level 3 for safe key storage and cryptographic operations. Azure Dedicated HSM offers customer key isolation and includes capabilities such as key backup and restoration, high availability, and scalability.
Google Cloud HSM: Google Cloud HSM is the hardware security module service provided by Google Cloud. It verifies HSMs to FIPS 140-2 Level 3 for secure key management. Google Cloud HSM offers a specialized key management service that includes capabilities including key backup and restoration, high availability, and centralized key management.
Per Adobe and Microsoft requirements, it is required that cryptographic keys used for signing be stored in a compliant device, are non-exportable from the device, and have not been imported into the device. These requirements make using HSMs, either a customer-managed HSM, a cloud HSM service, or a cloud signing service like eSigner, a requirement.
To know more on how we provide support for Cloud HSMs, please visit our dedicated page.
Ordering Attestation and Certificates
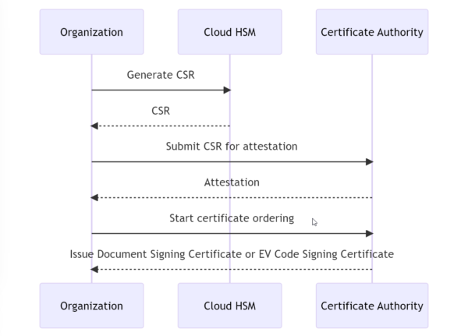
Since a cloud HSM is not operated and managed by the Certificate Authority, precise protocols must be followed to ensure the secure generation and storage of private keys. While some cloud HSM offerings can provide an out-of-the-box procedure for producing a key attestation proof for the keypairs of a certificate order, there are cloud HSM offerings which do not provide that capability. However, it is still possible to attest the proper key generation and key storage through a manual attestation and verification procedure. Let’s go over the essential steps:
Attestation criteria: To ensure the secure generation and storage of private keys within the HSM, a cybersecurity professional with adequate qualifications must act as an auditor to the key generation process and attest (hence the term “attestation”) that a key pair was generated and is stored in a compliant way in a compliant HSM device. In the case of SSL.com, attestation services can be provided for the cloud HSM services mentioned above. The attestation process typically ends with creating a Certificate Signing Request (CSR) and sending it to SSL.com for verification, after which the CSR is used to generate the ordered certificate.
Certificate Ordering: Organizations can begin the certificate ordering procedure once the private key generation and storage have been validated. The certified CSR is submitted to the certificate authority, which issues the document signing, OV, or EV code signing certificate.
For more information about certificate ordering and exploring options, visit our certificate ordering page at the following URL: SSL.com Certificate Ordering.
Cloud HSM Service Request Form
If you want to order digital certificates and view the customized pricing tiers for installation on a supported cloud HSM offering (AWS CloudHSM, Google Cloud Platform Cloud HSM, or Azure Dedicated HSM), please complete and submit the form below. After we receive your request, a member of SSL.com’s staff will contact you with more details about the ordering and attestation process.