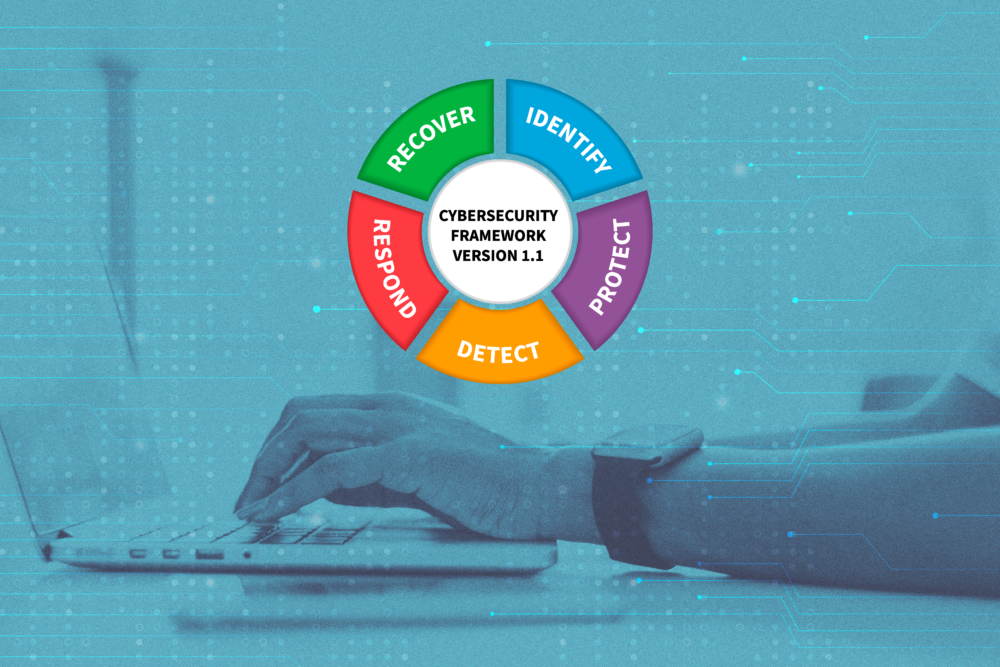
The National Institute of Standards and Technology’s (NIST) Cybersecurity Framework provides organizations with a systematic approach to understanding, managing, and reducing cybersecurity risk, thereby improving their overall cybersecurity posture.
The Framework, which is based on the five basic roles of Identify, Protect, Detect, Respond, and Recover, does not impose a strict structure but instead suggests a set of adaptable rules that may be customized according to the unique requirements, resources, and risk profiles of each company. This five-function model offers a comprehensive view of an organization’s management of cybersecurity risk over its full lifecycle.
Identify
The first core function, Identify, emphasizes the importance of understanding the business context, the resources supporting critical functions, and the related cybersecurity risks. This understanding is crucial as it provides a detailed overview of an organization’s digital ecosystem, enabling the formation of a focused and tailored risk management strategy. Activities in this phase might include asset identification and management, comprehensive risk assessment, and the development of a risk management strategy which serves as a blueprint for managing cybersecurity risks in the long run.
Protect
The second function, Protect, lays down the foundation for the implementation of safeguards to ensure the continued delivery of critical services. By designing and implementing appropriate safeguards, organizations can limit the adverse impact of potential cybersecurity events. This phase may comprise the implementation of advanced protective technologies, setting up effective access control mechanisms, and the establishment of robust information protection processes and procedures to guard against potential cyber threats.
Detect
The Detect function encompasses activities that allow organizations to identify the occurrence of a cybersecurity event quickly and accurately. Rapid detection is critical in the cyber domain as it can significantly reduce the potential damage caused by a cyber-incident. Typical activities in this phase include monitoring for anomalies and unusual events, implementing continuous security monitoring mechanisms, and designing efficient detection processes.
Respond
In the Respond phase, the emphasis shifts towards activities necessary to act once a cybersecurity incident is detected. A swift and effective response can often make the difference between a minor disruption and a major business crisis. Activities in this phase could include incident response planning, establishment of clear communication channels, comprehensive incident analysis, immediate incident mitigation, and subsequent improvements to prevent the recurrence of similar incidents.
Recover
Finally, the Recover function is all about resilience and restoration. This function helps organizations maintain their operations in the face of a cyber incident and restore any services or capabilities that were impaired. Key activities in this phase might include recovery planning, improvements to restore and enhance systems post-incident, and communication strategies to manage internal and external stakeholders during the recovery process.
Each of these core functions work in harmony, providing a comprehensive approach to cybersecurity risk management that balances proactive and reactive measures, creating a resilient digital environment.
Risk Management: A Strategic Approach to Cybersecurity
The NIST Cybersecurity Framework underscores the importance of adopting a risk-based approach to managing cybersecurity. By viewing cybersecurity through the lens of risk management, organizations can more effectively align their cybersecurity initiatives with their overall business objectives, strategically allocate resources, and enable informed decision-making.
Risk Management is not a singular activity but a continuous process that involves the recognition, assessment, and treatment of risks, followed by the monitoring of their mitigation measures for effectiveness. The essence of this process is to acknowledge that every organization has a unique risk profile, which should guide the selection and implementation of their cybersecurity measures.
Transitioning from the Current ‘As-Is’ to the Desired ‘To Be’ State
Transitioning from the current ‘as-is’ state to the desired ‘to-be’ state in line with the NIST Cybersecurity Framework involves a systematic, iterative process that is customized to each organization’s unique characteristics and circumstances. This process involves several key steps:
Prioritize and Scope
The first step involves the organization identifying its business objectives and system priorities. This includes understanding what digital assets the organization possesses, which are most critical to its operations, and what the potential impact would be if these assets were compromised. This step lays the groundwork for the upcoming actions by assisting the organization in determining what aspects of its operations it needs to focus on protecting the most.
Orient
This step involves identifying the related systems, stakeholders, regulatory requirements, and overall risk approach. It also encompasses identifying potential threats and vulnerabilities, conducting risk assessments, and establishing risk responses. A thorough understanding of the organization’s risk landscape is established during this phase.
Create a Current Profile
This is a snapshot of the organization’s current cybersecurity activities, capturing what controls and measures are currently in place. This profile serves as a baseline for the organization’s current cybersecurity posture and helps identify gaps between the current state and the desired state.
Conduct a Risk Assessment
This step involves a detailed analysis of the potential impact of identified risks based on the current profile. The evaluation should reflect potential business impacts from the occurrence of identified risks. This step is crucial as it helps the organization understand the actual risk it faces and the potential consequences, providing a foundation for informed decision-making about risk management.
Create a Target Profile
This profile outlines the organization’s desired cybersecurity outcomes based on its risk assessment, business objectives, and regulatory requirements. It essentially defines what the organization’s cybersecurity posture should look like in the future.
Determine, Analyze, and Prioritize Gaps
Here, the organization compares the current profile against the target profile to identify gaps. The identified gaps are analyzed based on risk, and a prioritized action plan is established. This action plan outlines the specific steps required to elevate the organization’s cybersecurity posture from its current state to its desired state.
Implement an Action Plan
In this final step, the organization implements the action plan, with ongoing monitoring to ensure that the plan is effectively improving the organization’s cybersecurity posture. This step involves acquiring necessary resources, implementing changes, and continually monitoring progress.
The journey from “as-is” to “to-be” is not a linear process but a cycle of continuous improvement. As the cybersecurity landscape evolves, organizations must revisit and revise their target profiles, assess new risks, and adjust their action plans as needed.
Case Studies: The NIST Cybersecurity Framework in Action
While the NIST Cybersecurity Framework provides a comprehensive guide to managing cybersecurity risk, it is often useful to look at real-world examples of how it has been implemented. Here are two case studies demonstrating how organizations have utilized the framework to improve their cybersecurity posture.
Case Study 1: Healthcare Organization
A large healthcare organization was looking to strengthen their cybersecurity measures due to the sensitive nature of the data they handle. By adopting the NIST Cybersecurity Framework, they initiated a detailed process to identify and protect their most crucial digital assets, which included patient records and other confidential data.
During the Orient phase, they identified key threats and vulnerabilities such as phishing attacks and potential data breaches. A current profile was created to capture their existing cybersecurity measures, revealing several gaps in their defenses.
A target profile was then created to outline their ideal cybersecurity posture, one that could effectively counter identified threats. Prioritized actions included implementing advanced encryption methods, strengthening access controls, and providing cybersecurity training to staff.
Since the implementation of their action plan, the organization has successfully thwarted numerous cyber threats, and continues to monitor and adapt their plan to address emerging threats, demonstrating the ongoing nature of the cybersecurity process.
Case Study 2: Financial Institution
A mid-size financial institution, faced with growing cyber threats and regulatory pressure, turned to the NIST Cybersecurity Framework to bolster their cybersecurity strategy.
The process started with a comprehensive risk assessment to identify their key digital assets and associated risks. The Detect function was particularly crucial due to the high-stakes nature of financial transactions, with the institution implementing continuous security monitoring mechanisms to detect anomalies.
A swift and efficient Respond function was also vital, leading the institution to develop a detailed incident response plan and establish clear communication channels for when incidents occurred.
The Recover function ensured that the institution could maintain operations in the face of an incident and restore any impaired services. This involved a comprehensive recovery plan and communication strategies to manage stakeholders during the recovery process.
The implementation of the NIST Cybersecurity Framework led to significant improvements in the financial institution’s cybersecurity posture, illustrating the framework’s adaptability across different industries.
Practical Tools for Implementing the NIST Cybersecurity Framework
While the NIST Cybersecurity Framework outlines a systematic approach to managing cybersecurity risks, practical tools are needed to facilitate the implementation of the Framework. Here, we’ll cover some tools that are commonly used across the five core functions of the Framework: Identify, Protect, Detect, Respond, and Recover.
Identify
For the Identify function, organizations need tools that can assist with asset discovery and risk assessment.
-
Nmap: This is a powerful network mapping tool that can discover devices on a network and uncover open ports and services that might be susceptible to attack.
-
Risk Management Software: Tools like RSA Archer and LogicGate Risk Cloud can assist in identifying and assessing cybersecurity risks.
Protect
The Protect function involves tools that can help in creating barriers against potential cyber threats.
-
Firewalls and Intrusion Prevention Systems (IPS): Tools like Cisco ASA, Palo Alto Networks firewalls, and Fortinet FortiGate provide robust network defenses.
-
Antivirus and Anti-malware Software: Solutions like Norton, Bitdefender, or Kaspersky can help to protect systems from malicious software.
-
Access Control Tools: Tools like Microsoft Active Directory or Okta can help manage user identities and enforce access controls.
- Pre-Signing Malware Scans: eSigner by SSL.com offers scanning of documents for malware before allowing electronic signatures, preventing malicious code from spreading through digitally signed documents.
Detect
Detection tools help to uncover potential cybersecurity incidents.
-
Intrusion Detection Systems (IDS): Tools such as Snort or Suricata can detect anomalous activity that might indicate an attack.
-
Security Information and Event Management (SIEM) Tools: Platforms like Splunk or LogRhythm can aggregate and analyze log data from various sources to detect potential security incidents.
Respond
When an incident occurs, response tools assist organizations in taking swift action.
-
Incident Response Platforms: Tools like IBM Resilient Incident Response Platform or D3 Security can streamline the incident response process, ensuring a rapid and coordinated response.
Recover
Recovery tools help organizations restore their services following a cybersecurity incident.
-
Backup and Recovery Tools: Solutions like Veeam or Veritas can facilitate the process of recovering data following a cybersecurity incident.
-
Disaster Recovery Tools: Platforms like Zerto or VMware Site Recovery can help organizations recover their entire IT infrastructure following a major incident.
Remember that the tools alone are not enough. They must be integrated into a comprehensive cybersecurity strategy, like the one outlined by the NIST Cybersecurity Framework, to be truly effective.
Last thoughts: Cybersecurity with SSL.com as Your Guide
With cybersecurity threats on the rise, businesses need an adaptable strategy and trusted partner. SSL.com provides customized solutions aligned with the NIST Cybersecurity Framework to help safeguard your valuable digital assets.
This video summarizes how to implement the NIST Framework
Our experts become trusted advisors, guiding you through each step of bolstering your defenses. We take the time to understand your unique needs and goals, offering insights tailored specifically to your business.
Don’t leave your company exposed. Partner with a proven leader devoted to creating a secure digital ecosystem. SSL.com has the experience to provide the cybersecurity solutions and support your business needs.


