IRS extends its temporary acceptance of electronic or digitally-signed forms until 2023
Due to the continuing threat caused by the COVID-19 virus when it comes to face-to-face contact, the IRS, through Memorandum NHQ-10-1121-0005, has extended its acceptance of electronic or digitally-signed forms until 2023.
The memorandum expanded the list of IRS forms that can be remotely signed to at least 32. These forms include Form 1042, Annual Withholding Tax Return for US Source Income of Foreign Persons. Form 8832, Entity Classification Election and Internal Revenue Code Section 83(b) election statements.
The IRS notes that: “Electronic and digital signatures appear in many forms when printed and may be created by many different technologies. No specific technology is required for this purpose during this temporary deviation.” As commented on by Sarah-Jane Morin and Nicola Y. Liu of Morgan Lewis, this disclaimer by IRS signifies that it will accept scanned or photographed images of signatures as well as encryption-based or digital signatures.
As a trusted authority when it comes to digital signing services, we at SSL.com recommend that the IRS put out stricter rules when it comes to acceptable remote signatures. Tax forms are particularly sensitive forms of documents because they involve money and so issues might arise like taxpayers claiming that their signatures have been forged or the IRS might end up rejecting images of handwritten signatures or those that have been signed on touch screen devices because they do not accurately match what is in their records. The back-and-forth situations that a loose setup might cause can add up in terms of numbers and cause hassling situations to both citizens and the IRS.
We recommend that digital signatures be the IRS standard when it comes to acceptable remote signatures for the following reasons: 1) they strongly prove the identity of the person submitting the document; 2) they provide irrefutable evidence of non-tampering while the documents are in transit; 3) they are compliant with the US Federal ESIGN act.
IoT growth in recent years pushes for developments in PKI technology
US-based households and organizations have been observed to increase their usage of IoT objects – electronic devices that can connect and share data with other devices, through the internet.
“Last year, US households had on average 25 connected devices each, compared to 11 in 2019, according to a Deloitte survey. Global shipments of traditional PCs, including desktops, notebooks and workstations, also saw double digit growth rates last year as companies and schools invested in remote working and learning, according to research firm IDC.
In 2020, the average number of digital certificates organisations issued or acquired surged 43 per cent from 39,197 in 2019 to 56,192, according to the same report published last year. While that growth slowed significantly this year to just 4.3 per cent, according to this year’s report, machine identities now outnumber human identities thanks to the growth of IoT devices, cloud services and new applications.”
Additionally, it has been observed that “many businesses lack the resources and skills to manage their digital certificates.” This is an alarming fact because just one improperly-secured device can be used as an entry by cybercriminals to wreak havoc to a company’s IT infrastructure.
The growth of IoT usage requires an increased need for organizations to acquire professional PKI services in order to bulletproof their cybersecurity and properly manage their digital certificates. Recall that the catastrophic May 2021 Colonial Pipeline Ransomware attack was enabled by an employee login of a legacy Virtual Private Network (VPN) system that was set up with only single factor authentication.
SSL.com set to release eSigner CKA this January 2022
For the previous months, SSL.com has been developing an innovative program intended to help protect software publishers and users from malware hackers.
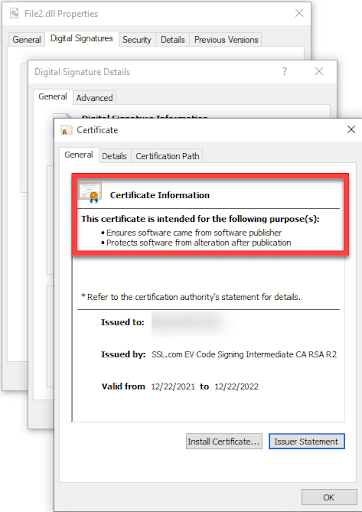
To open the new year, we are proud to offer eSigner CKA (Cloud Key Adapter) to our customers. eSigner CKA (Cloud Key Adapter) is a Windows based application that uses the CNG interface (KSP Key Service Provider) to allow tools such as certutil.exe and signtool.exe to use the eSigner Cloud Signing Service for Extended Validation Code Signing operations for software installers.
As our customers know, eSigner allows the integration of globally trusted digital signatures and timestamps to software, thus ensuring that it really came from the software publisher and protects it from being altered by hackers upon its release.
The eSigner CKA application adds practical options when it comes to digital signing by acting like a virtual USB token and loads the code signing certificates to the User certificate store. This feature helps make our eSigner cert more accessible with options to automate that doesn’t require intense research and procedures on the part of software publishers. Below is a sneak-peak of a sample file that has undergone EV Code Signing using eSigner CKA:
SSL.com provides a wide variety of SSL/TLS server certificates for HTTPS websites.


