Create a Jenkins file and define the pipeline on your code editor
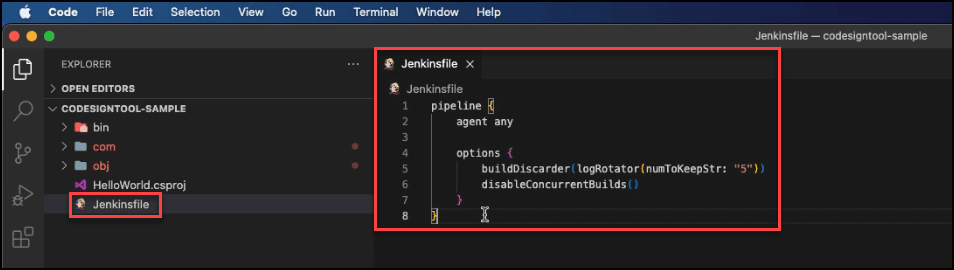
pipeline {
agent any
options {
buildDiscarder(logRotator(numToKeepStr: "5"))
disableConcurrentBuilds()
}
Set the .NET tool on your code editor by configuring Jenkins
Click the Manage Jenkins tab on your Jenkins dashboard.

Scroll down the page and click Global Tool Configuration.

Scroll down and click .NET SDK Installations.

Copy the value for .NET SDK and paste it on your code editor.


tools {
dotnetsdk "DOTNET_CORE_3.1.24"
}
Go to plugins.jenkins.io and install the .NET SDK plugin

Under Manage Jenkins on your Dashboard, check Manage Plugins to confirm if the .NET SDK plugin has been installed.


After confirming that the plugin has been installed, go back to .NET SDK INSTALLATIONS and make sure the correct version and release details of the .NET SDK plugin are set. Proceed to click the Save button.

Set the Environment Variables on your code editor

environment {
USERNAME = credentials('es-username') // SSL.com account username.
PASSWORD = credentials('es-password') // SSL.com account password.
CREDENTIAL_ID = credentials('es-crendential-id') // Credential ID for signing certificate.
TOTP_SECRET = credentials('es-totp-secret') // OAuth TOTP Secret (https://www.ssl.com/how-to/automate-esigner-ev-code-signing)
ENVIRONMENT_NAME = 'PROD' // SSL.com Environment Name. For Demo Account It can be 'TEST' otherwise it will be 'PROD'
}
You will find the values for each variable on your Jenkins dashboard under Security > Manage Credentials.



Set the stages for creating artifacts directory, pulling docker image, building .NET, and code signing the artifact

1) Create Artifact Directory for store signed and unsigned artifact files.
stage('Create artifacts directory') {
steps {
sh 'mkdir ${WORKSPACE}/artifacts'
sh 'mkdir ${WORKSPACE}/packages'
}
}
2) Pull Codesigner Docker Image From Github Registry.
stage('Docker Pull Image') {
steps {
sh 'docker pull ghcr.io/sslcom/codesigner:latest'
}
}
3) Build a dotnet project or solution and all of its dependencies. After the dll or exe file has been created, copy to ‘packages’ folder for signing.
stage('Build Dotnet') {
steps {
sh 'dotnet build dotnet/HelloWorld.csproj -c Release'
sh 'cp dotnet/bin/Release/netcoreapp3.1/HelloWorld-0.0.1.dll ${WORKSPACE}/packages/HelloWorld.dll'
}
}
4) This is the step where the created DLL (artifact) files will be signed with CodeSignTool.
stage('Sign and Save Dotnet Core DLL Artifact') {
steps {
sh 'docker run -i --rm --dns 8.8.8.8 --network host --volume ${WORKSPACE}/packages:/codesign/examples --volume ${WORKSPACE}/artifacts:/codesign/output
-e USERNAME=${USERNAME} -e PASSWORD=${PASSWORD} -e CREDENTIAL_ID=${CREDENTIAL_ID} -e TOTP_SECRET=${TOTP_SECRET} -e ENVIRONMENT_NAME=${ENVIRONMENT_NAME}
ghcr.io/sslcom/codesigner:latest sign -input_file_path=/codesign/examples/HelloWorld.dll -output_dir_path=/codesign/output'
}
post {
always {
archiveArtifacts artifacts: "artifacts/HelloWorld.dll", onlyIfSuccessful: true
}
}
}
}
}
Create a Github repo
Copy each of the push command components on Github.
Write the commands at a new terminal on your code editor to push the code.

After pushing the code, go to your Github account and copy the URL link of your project.

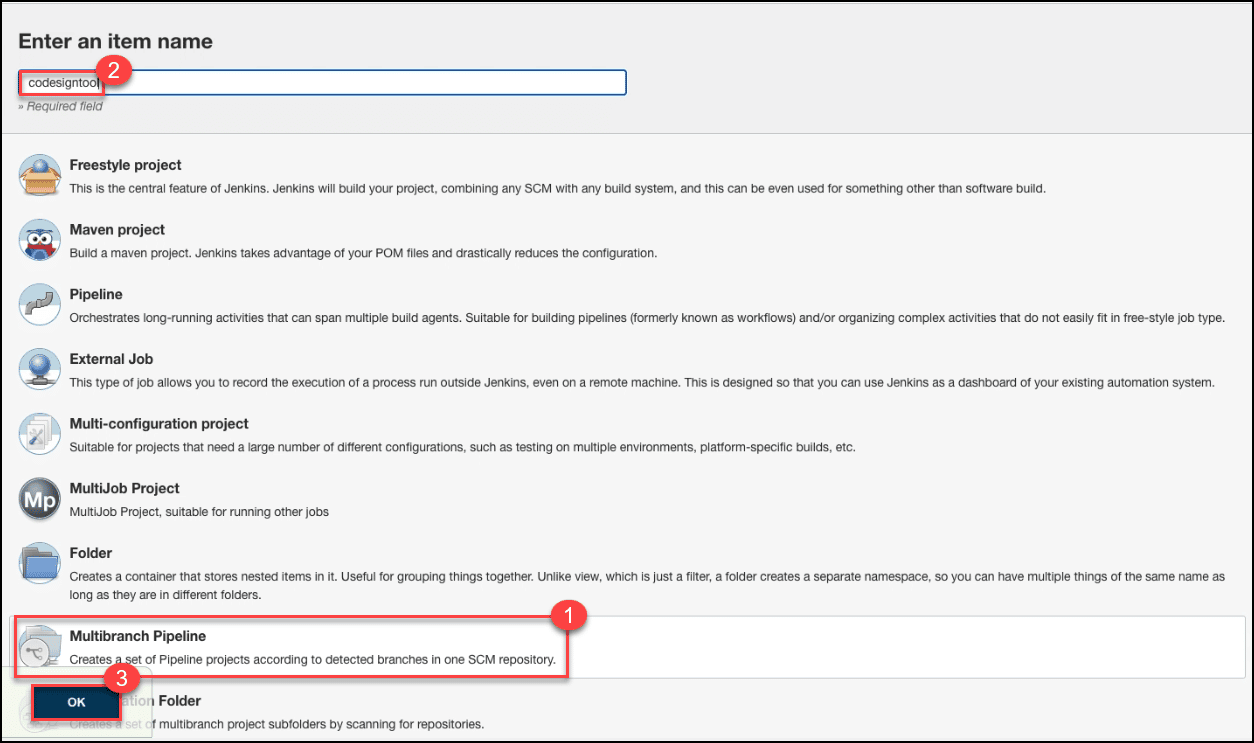
Proceed to your Jenkins account and click the Create a job link.

Choose Multibranch Pipeline, set the name for your project, and click the OK button.
Under Branch Sources, select Git and paste the URL link of your Github project.

Scroll down to Scan Multibranch Pipeline Triggers. Check the box for Periodically if not otherwise run. You can select 2 minutes.

Click the Save button.

Go back to your Jenkins account, click on your project, and confirm if the pipeline has started

Click on your Jenkins project and select Scan Multibranch Pipeline Now on the Dashboard.

Click Console Output

Scroll down and check if code signing is successful

Entire Script
Define the pipeline
pipeline {
agent any
options {
buildDiscarder(logRotator(numToKeepStr: "5"))
disableConcurrentBuilds()
}
Install Build Tools
tools {
dotnetsdk "DOTNET_CORE_3.1.24" //https://plugins.jenkins.io/dotnet-sdk
}
Create an environment variable
environment {
USERNAME = credentials('es-username') // SSL.com account username.
PASSWORD = credentials('es-password') // SSL.com account password.
CREDENTIAL_ID = credentials('es-crendential-id') // Credential ID for signing certificate.
TOTP_SECRET = credentials('es-totp-secret') // OAuth TOTP Secret (https://www.ssl.com/how-to/automate-esigner-ev-code-signing)
ENVIRONMENT_NAME = 'PROD' // SSL.com Environment Name. For Demo Account It can be 'TEST' otherwise it will be 'PROD'
}
Script for the Build and Sign Stages
stages {
// 1) Create Artifact Directory for store signed and unsigned artifact files
stage('Create artifacts directory') {
steps {
sh 'mkdir ${WORKSPACE}/artifacts'
sh 'mkdir ${WORKSPACE}/packages'
}
}
// 2) Pull Codesigner Docker Image From Github Registry
stage('Docker Pull Image') {
steps {
sh 'docker pull ghcr.io/sslcom/codesigner:latest'
}
}
// 3) Build a dotnet project or solution and all of its dependencies.
// After it has been created dll or exe file, copy to 'packages' folder for signing
stage('Build Dotnet') {
steps {
sh 'dotnet build dotnet/HelloWorld.csproj -c Release'
sh 'cp dotnet/bin/Release/netcoreapp3.1/HelloWorld-0.0.1.dll ${WORKSPACE}/packages/HelloWorld.dll'
}
}
// 4) This is the step where the created DLL (artifact) files will be signed with CodeSignTool.
stage('Sign and Save Dotnet Core DLL Artifact') {
steps {
sh 'docker run -i --rm --dns 8.8.8.8 --network host --volume ${WORKSPACE}/packages:/codesign/examples --volume ${WORKSPACE}/artifacts:/codesign/output
-e USERNAME=${USERNAME} -e PASSWORD=${PASSWORD} -e CREDENTIAL_ID=${CREDENTIAL_ID} -e TOTP_SECRET=${TOTP_SECRET} -e ENVIRONMENT_NAME=${ENVIRONMENT_NAME}
ghcr.io/sslcom/codesigner:latest sign -input_file_path=/codesign/examples/HelloWorld.dll -output_dir_path=/codesign/output'
}
post {
always {
archiveArtifacts artifacts: "artifacts/HelloWorld.dll", onlyIfSuccessful: true
}
}
}
}
}
Sample Jenkins Pipeline
Check out the sample Jenkins pipeline we have created on github.com/SSLcom/codesigner-jenkins-sampleOther Remote Signing Integration Guides
- Cloud Code Signing Integration with CircleCI
- Cloud Code Signing Integration with GitHub Actions
- Cloud Code Signing Integration with GitLab CI
- Cloud Code Signing Integration with Travis CI
- Cloud Code Signing Integration with Azure DevOps
- Cloud Code Signing Automation with CI/CD Services
Need Custom Solutions?
With our expert knowledge and five-star support staff, we’re ready and willing to work with you on custom solutions or enterprise-level high-volume signing discounts. Fill out the form below and we’ll be in touch.






















