Environment Variables
- USERNAME: SSL.com account username. (Required)
- PASSWORD: SSL.com account password (Required)
- CREDENTIAL_ID: Credential ID for signing certificate. If credential_id is omitted and the user has only one eSigner code signing certificate, CodeSignTool will default to that. If the user has more than one code signing certificate, this parameter is mandatory. (Required)
- TOTP_SECRET: OAuth TOTP Secret. You can access detailed information on https://www.ssl.com/how-to/automate-esigner-ev-code-signing (Required)
- ENVIRONMENT_NAME : ‘TEST’ or ‘PROD’ Environment. (Required)
Inputs
- input_file_path: Path of code object to be signed. (Required)
- output_dir_path: Directory where signed code object(s) will be written. If output_path is omitted, the file specified in -file_path will be overwritten with the signed file.
Java Code (Maven) JAR Signing Example Workflow
Create a project
Under the project, create a file for Travis
Define the components of the workflow
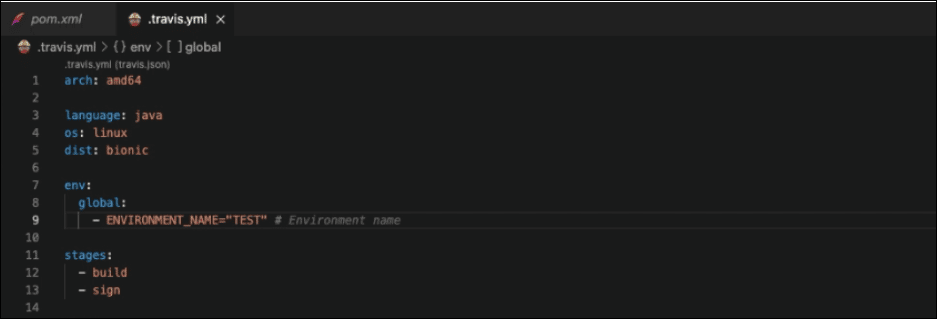
- Place the CPU Architecture to run the job on
arch: amd64
- Default language to run tests in
language: java
- Specify the operating system to run the job on
os: linux
- Write the Ubuntu distribution that will be used
dist: bionic
- Define environment variables globally. Job level property overrides global variables.
- Take note that TERM=dumb is only needed for Gradle project instances.
- Under ENVIRONMENT_NAME, place “TEST” for test signing, and “PROD” for live signing.
env:
global:
– PROJECT_NAME=”HelloWorld”
– PROJECT_VERSION=”0.0.1″
– TERM=dumb
– ENVIRONMENT_NAME=”TEST”
- Specify the order of stages. All jobs in one stage must be completed before the next stage is executed.
stages:
– build
– sign
Outline the build stage
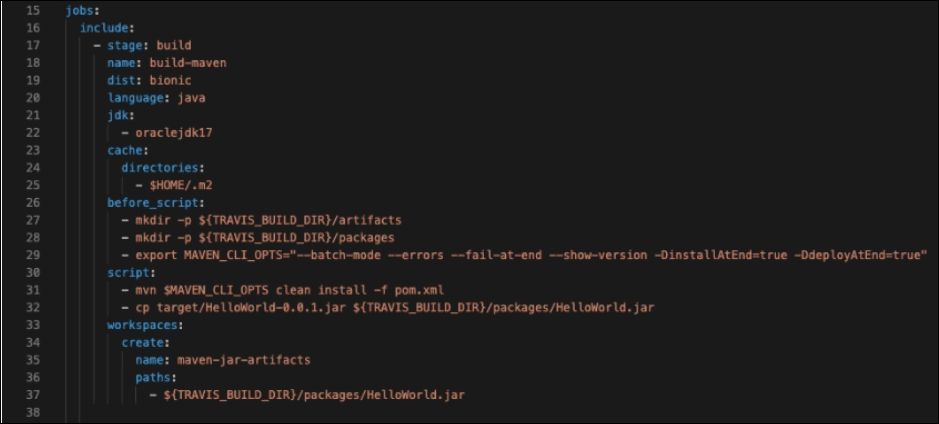
jobs:
include:
– stage: build
- The job name
name: build-maven
- The Ubuntu distribution to use
dist: bionic
- Use docker command for signing
services:
– docker
- Use dotnet-cli to build the project
language: java
- Java version to build the project
jdk:
– oraclejdk17
- Cache m2 directory in order to speed up
cache:
directories:
– $HOME/.m2
- Write the Before script to run before building the project
before_script:
# Create directories for artifacts
– mkdir -p ${TRAVIS_BUILD_DIR}/artifacts
– mkdir -p ${TRAVIS_BUILD_DIR}/packages
# Set Maven build options
– export MAVEN_CLI_OPTS=”–batch-mode –errors –fail-at-end –show-version -DinstallAtEnd=true -DdeployAtEnd=true”
- Write the script to build the project.
- In this signing example workflow, multiple project types were created. This is why files of different project types were kept by creating subfolders. A subfolder named ‘java’ was created for Java projects. In the demo screenshot above, there was no need to create a subfolder named ‘java’ so this was not included in the script.
script:
# Build Maven project with Maven Options
– mvn $MAVEN_CLI_OPTS clean install -f java/pom.xml
# Copy built artifacts to artifacts directory
– cp java/target/${PROJECT_NAME}-${PROJECT_VERSION}.jar ${TRAVIS_BUILD_DIR}/packages/${PROJECT_NAME}.jar
- Outline how to specify a list of files and directories that should be attached to the job if it succeeds.
workspaces:
create:
name: maven-jar-artifacts
paths:
# Save artifact in order to use signing job
– ${TRAVIS_BUILD_DIR}/packages/${PROJECT_NAME}.jar
Outline the sign stage
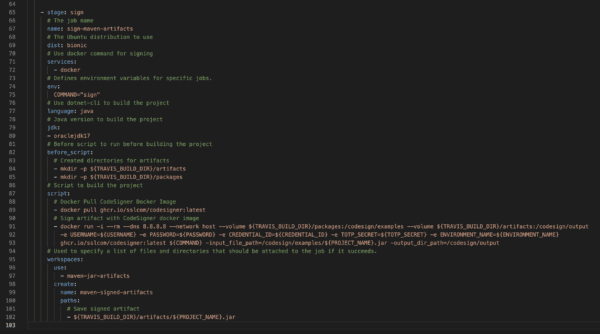
– stage: sign
- Write the job name
name: sign-jar-file
- Place the Ubuntu distribution to use
dist: bionic
- Use Docker command for signing
services:
– docker
- Define environment variables for specific jobs.
- In the screenshot above, the sign command was defined directly in the sign script and not under environment variables. Both methods can sign correctly with TravisCI.
env:
COMMAND=”sign”
- Use dotnet-cli to build the project
language: java
- Java version to build the project
jdk:
– oraclejdk17
- Before script to run before building the project
before_script:
# Create directories for artifacts
– mkdir -p ${TRAVIS_BUILD_DIR}/artifacts
– mkdir -p ${TRAVIS_BUILD_DIR}/packages
- Script to build the project
script:
# Docker Pull CodeSigner Docker Image
– docker pull ghcr.io/sslcom/codesigner:latest
# Sign artifact with CodeSigner Docker image
– docker run -i –rm –dns 8.8.8.8 –network host –volume ${TRAVIS_BUILD_DIR}/packages:/codesign/examples
–volume ${TRAVIS_BUILD_DIR}/artifacts:/codesign/output
-e USERNAME=${USERNAME} -e PASSWORD=${PASSWORD} -e CREDENTIAL_ID=${CREDENTIAL_ID} -e TOTP_SECRET=${TOTP_SECRET}
-e ENVIRONMENT_NAME=${ENVIRONMENT_NAME} ghcr.io/sslcom/codesigner:latest ${COMMAND}
-input_file_path=/codesign/examples/${PROJECT_NAME}.jar -output_dir_path=/codesign/output
- Used to specify a list of files and directories that should be attached to the job if it succeeds.
workspaces:
use:
– maven-jar-artifacts
create:
name: signed-jar-file
paths:
# Save signed artifact
– ${TRAVIS_BUILD_DIR}/artifacts/${PROJECT_NAME}.jar
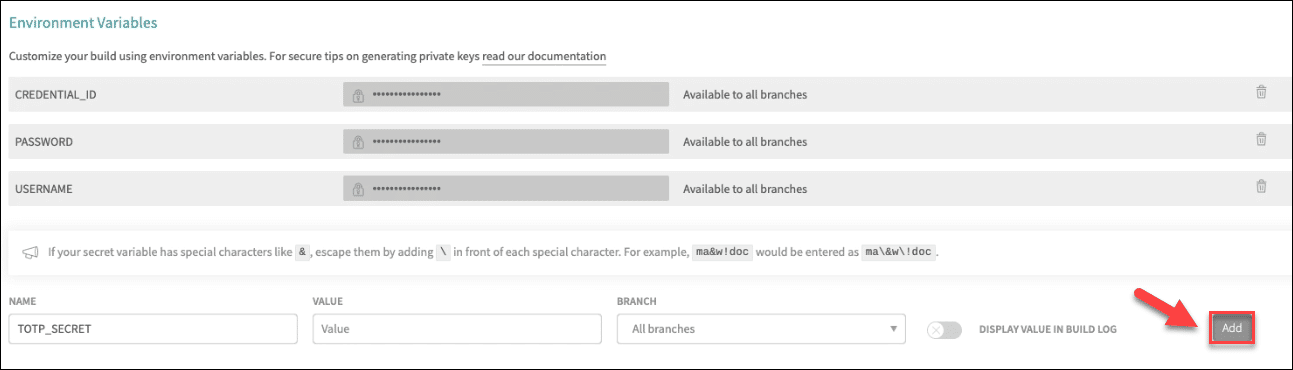
Define the Environment Variables
Go to Travis and click the Settings button

Add the value for each variable
Scroll down to the Environment Variables section and click the Add button to add the value for each variable
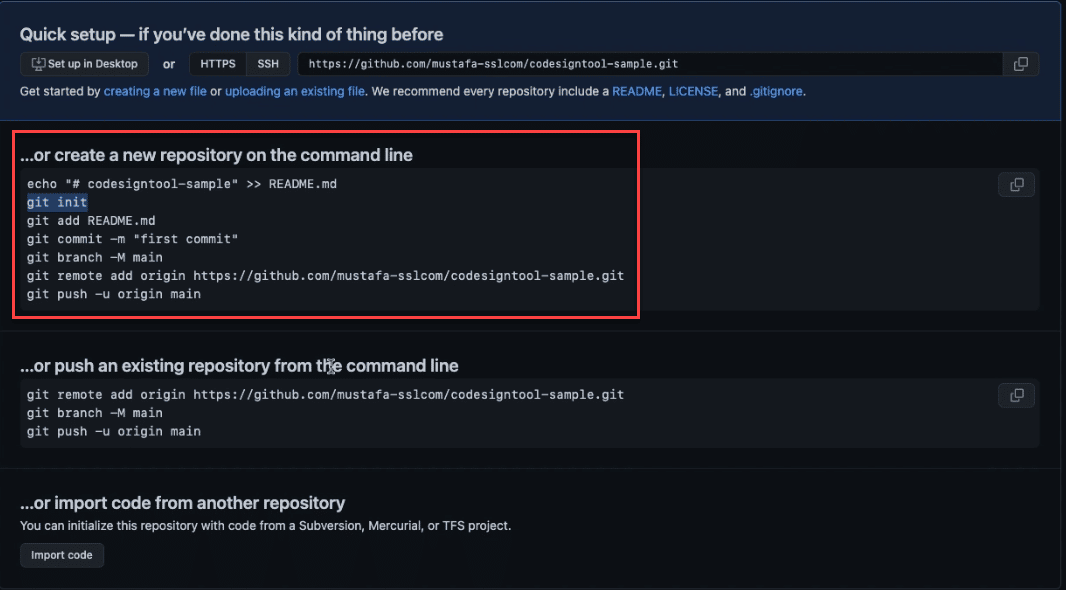
Create a Github repo
Look for the push commands on Github
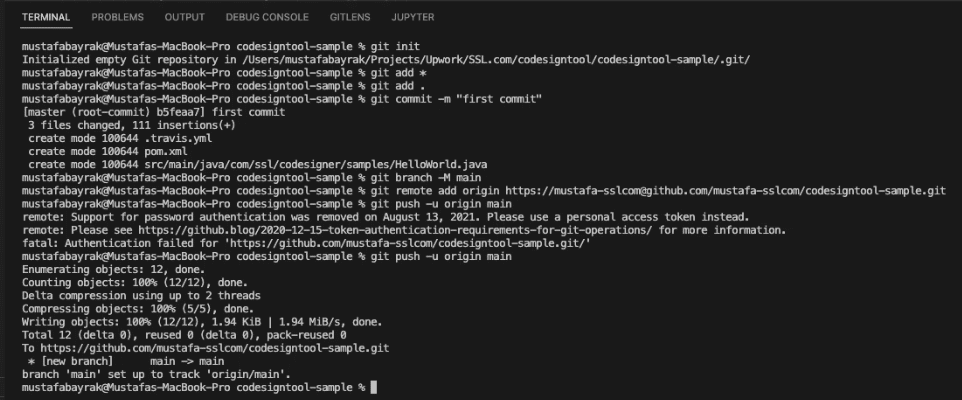
Write the push commands at a terminal on your editor
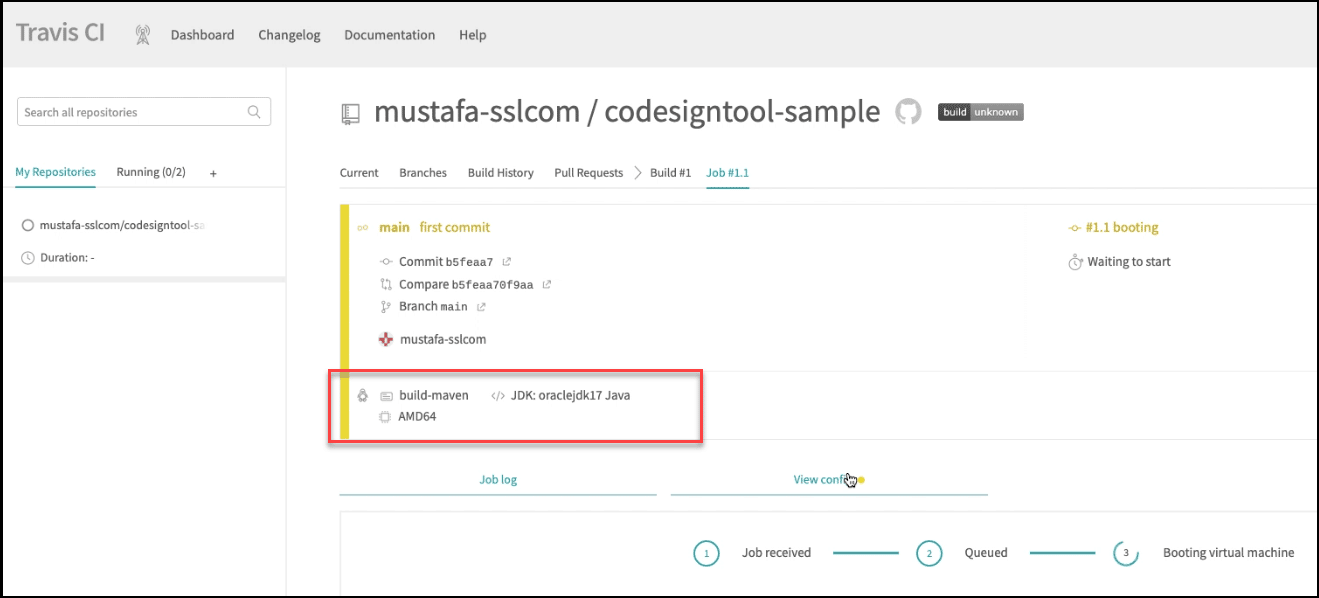
Wait for the build job to be completed
On Travis, the build job should start automatically after you have pushed the code.
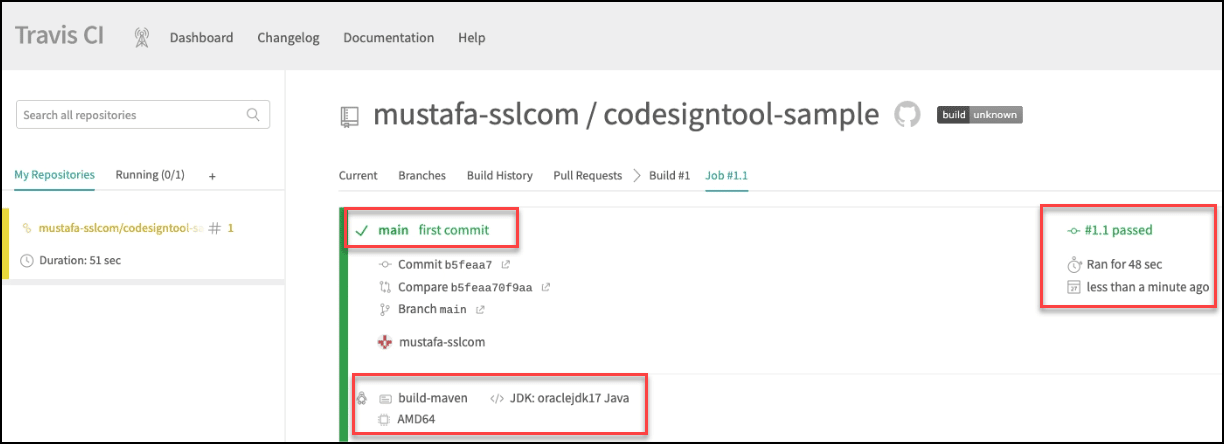
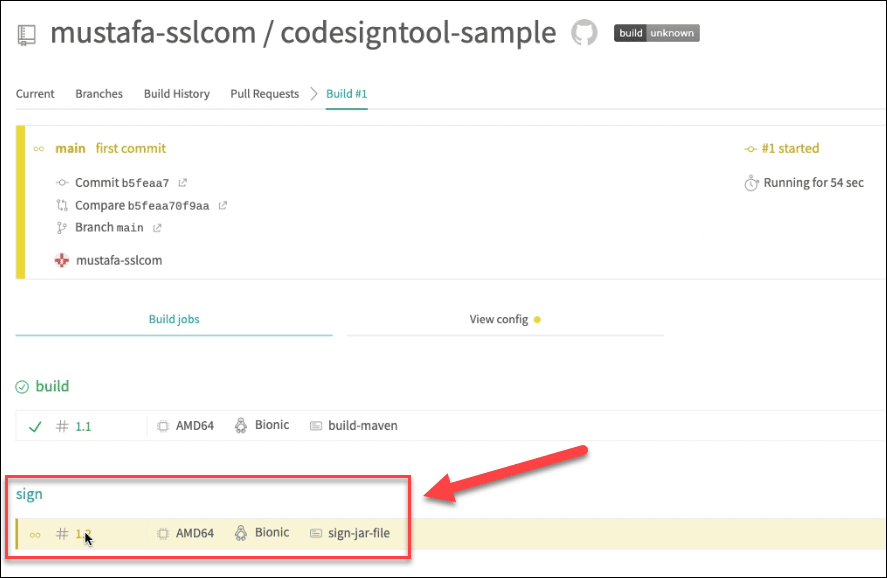
Initiate the code signing stage
Click the sign section for CodeSignTool to start the signing process
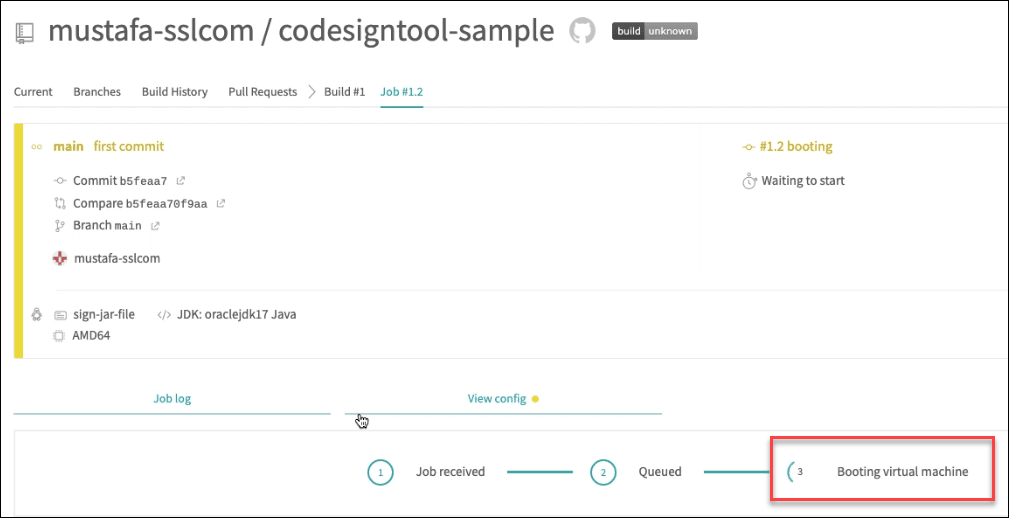
Wait for your virtual machine to finish booting
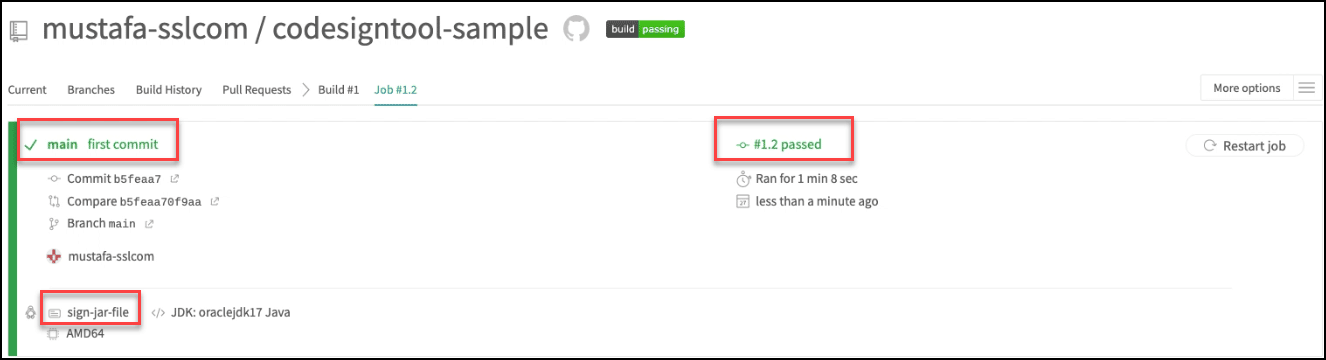
Confirm if code signing is successful
Sample Travis CI Pipeline
Check out the sample Travis CI pipeline we have created on github.com/SSLcom/codesigner-travisci-sampleOther CI/CD Service Remote Signing Integration Guides
- Cloud Code Signing Integration with CircleCI
- Cloud Code Signing Integration with GitHub Actions
- Cloud Code Signing Integration with GitLab CI
- Cloud Code Signing Integration with Jenkins CI
- Cloud Code Signing Integration with Azure DevOps
- Cloud Code Signing Integration with BitBucket
- Cloud Code Signing Automation with CI/CD Services
Need Custom Solutions?
With our expert knowledge and five-star support staff, we’re ready and willing to work with you on custom solutions or enterprise-level high-volume signing discounts. Fill out the form below and we’ll be in touch.


